_story.jpg)
A new variant of the Ursnif banking trojan, also known as Gozi, is apparently tricking unwary victims and stealing their information by attacking under the guise of a harmless captcha. The report comes from BleepingComputer who had received the information from security researchers at MalwareHunterTeam.
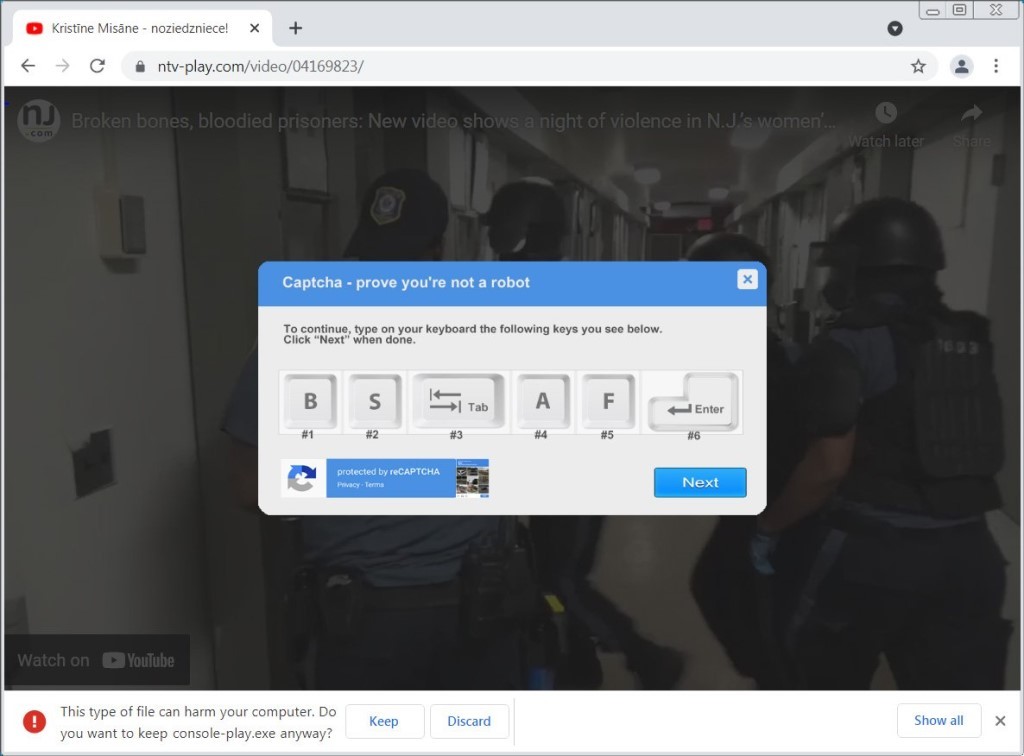
Apparently, when trying to watch a certain embedded YouTube video whose content is related to a violent night in a women's prison in New Jersey via a URL, a file named "console-play.exe", which serves the malware, is downloaded. This happens when you press the play on the said YouTube NJ women's prison video.
After that, a fake reCAPTCHA is displayed that asks the user to press certain buttons to prove they aren't a bot. Also since the console-play.exe is an executable file, the browser warns the user of potential malware threats.
However, the reCAPTCHA plays its part here in order to trick the unsuspecting user. It asks the user to press the B, S, Tab, A, F, and finally the Enter keys. And while the B, S, A, and F are simply used as decoys, the Tab key highlights the "Keep" button on the browser malware warning. And once the Enter is placed, the user perhaps unknowingly welcomes the Ursnif trojan-distributing malicious file.
And the video will apparently start playing after this is done making the user proud of themself that they are indeed not a robot.
If the downloaded console-play.exe is run, a folder is created in Roaming under the AppData directory. This folder is named "Bouncy for .NET Helper" and has plenty of decoy files in it other than the main malware containing executable called "BouncyDotNet.exe".
Apparently, the BouncyDotNet.exe is able to create the infectious DLL file that helps the Ursnif trojan spread. The trojan can steal information related to credentials and such.
This isn't the first instance of an Ursnif attack this year as Avast reported back in March that the malware had hit over 100 banks in Italy.
Source and images: BleepingComputer




















6 Comments - Add comment